Digital Credentials
explained
Discover the Power of Digital Credentials: Assurance, Efficiency, Privacy
Are you struggling to trust data you receive? Or protect the integrity of data you share? Then read on!
Digital credential solutions establish trust between parties – individuals, authorities, businesses, devices – by enabling them to automatically verify the authenticity of data and documents and confidently exchange them and work together more effectively.
In essence, they are digitally signed data files that can be automatically processed and verified.
A credential is a piece of information that shows someone’s qualification, achievement, or attribute. It can be anything from a driver’s license or diploma to a salary statement or event-ticket.
A verifiable credential is a datafile that contains specific data. It’s cryptographically secured, digitally signed, by one or more trusted issuers. The data is machine-verifiable and therefor tamper-evident.
Verifiable credentials are also privacy preserving. The owner of a verifiable credential has complete control over it and can decide whether to share it with others or not. By using a so-called Credential Wallet, the owner can prove specific qualifications or attributes without revealing any unnecessary personal information.
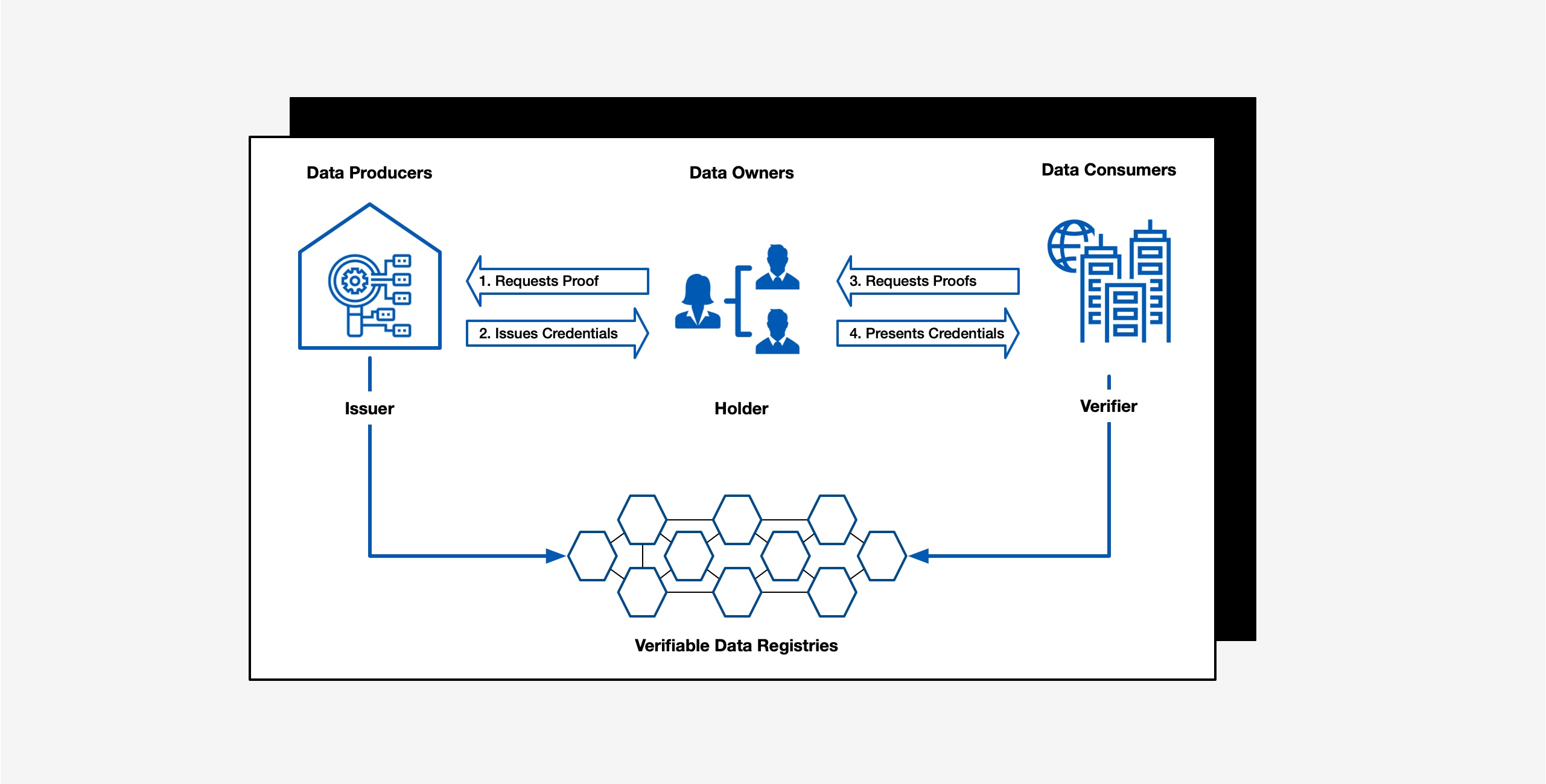
How do Verifiable Credentials work
Verifiable Credentials allow individuals and organizations to share only the necessary information while maintaining control over their personal data.
1. The Holder — the person, organization, or subject — requests certain data that prove something about them, like f.i. a drivers license, address or permit, from some authority, like the DMV or local municipality.
2. The Issuer — the authority, authentic source, or other data-producer — issues this data as a Verifiable Credential and offers this to the Holder, who stores it in their personal credential wallet.
3. At a later time, another party, the Verifier — like an authority, company, or other data-processor — can request a proof or certain data from the Holder. In our example f.i. that they have a permit to hold a street-fair.
4. The Holder shares the proof or data as a Verifiable Presentation with the requesting party, who can immediately verify that the data is authentic, valid and has not been tampered with.
Organizational credentials
Organizations have lots of credentials that they have to share regularly with other parties:
- Purchase Orders and Invoices
- Chamber of Commerce certificate
- Ultimate Beneficial Owner (UBO) attestations
- Export and supply chain data and documents
- Digital Product Passports
- Tax or VAT code and compliance with tax obligations
- Accountant statements
- Bank account information
- Certifications, permits and licenses
- Legal Entity Identifier and DUNS numbers
- etc
Examples of personal data credentials
People have lots of credentials that they have to share regularly with other parties:
- Identities
- Drivers license
- Professional certifications and licenses
- College and university degrees
- Academic transcripts
- Employment records
- Employer’s declarations
- Permits and licenses
- Medical records and prescriptions
- Credit reports
- Insurance policies
- Property deeds
- Financial statements
- Travel and immigration documents
- Background checks
- Drug test results
- Security clearances and access rights
- etc.
Download the Sphereon Wallet for free and try it yourself:
Sphereon Wallet Demo 🔗
More information
If you want to know more about this technology, there are a growing amount of sources:
- W3C Verifiable Credential specification
- W3C Verifiable Credentials Working Group
- EU EBSI Verifiable Credentials Explained
- UNECE White Paper on eDATA Verifiable Credentials for Cross Border Trade
- John Savill’s Technical Training ‘Understanding and Using Verifiable Credentials’
Awesome detailed technical deep-dive. 1h32m, but then you know more than most.
or just contact us!