European
Business Wallet
Unlocking seamless digital business interactions!
The 4Sure Business Wallet is our enterprise-grade solution tailored to align with the European Commission’s vision for the digital transformation of business.
As part of the EU’s Digital Decade and the Competitiveness Compass 2025, the European Business Wallet aims to empower businesses to operate more efficiently and securely across borders.
At 4Sure, we deliver on that promise with a solution that combines regulatory-grade trust infrastructure with flexible deployment models, to be used in complex ecosystems.
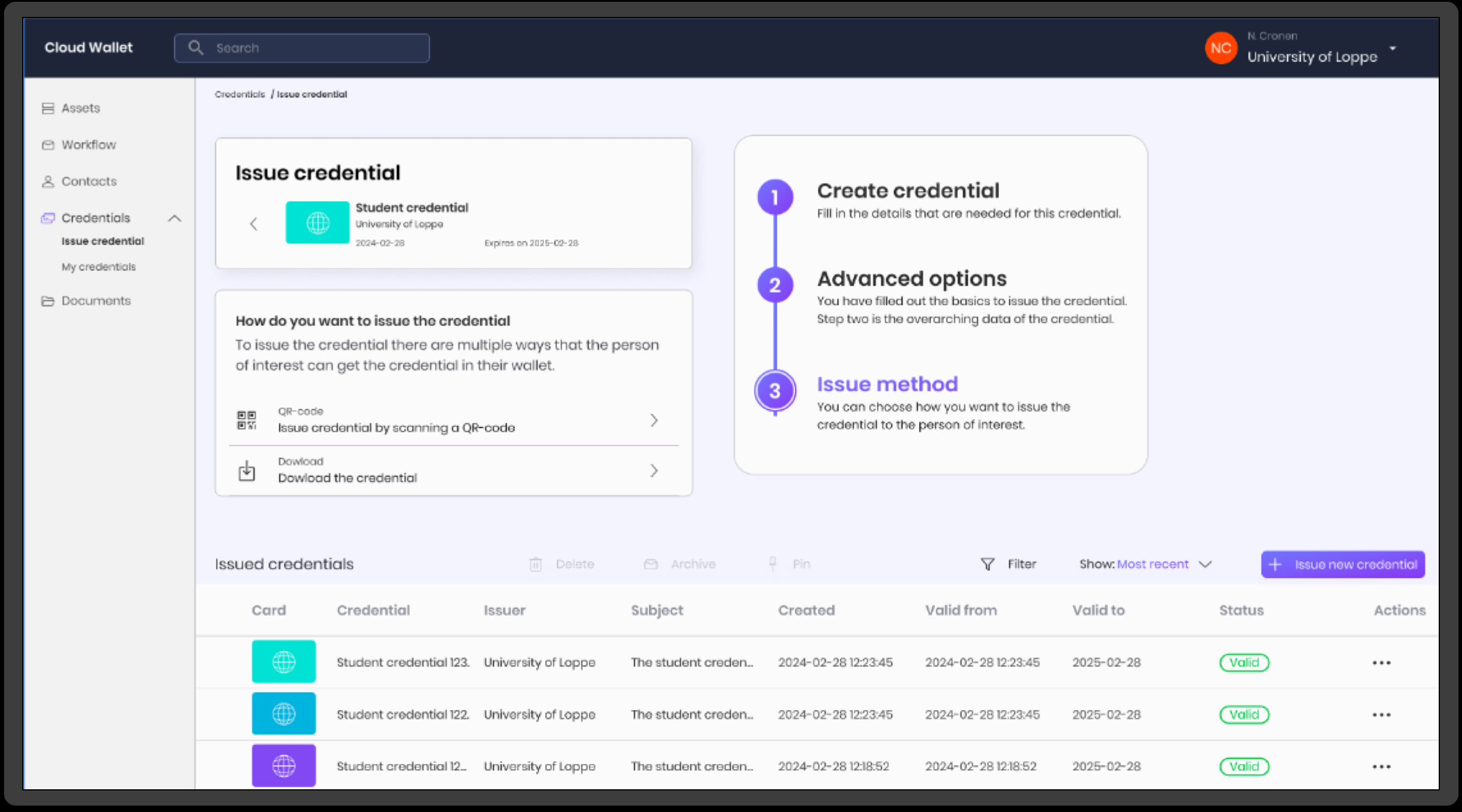 The European Business Wallet (EBW) is a web-based digital wallet designed to simplify business operations in the EU by enabling organizations to store, present, and verify official digital credentials. These may include licenses, permits, attestations, and certificates: secured, tamper-proof, and instantly verifiable.
The European Business Wallet (EBW) is a web-based digital wallet designed to simplify business operations in the EU by enabling organizations to store, present, and verify official digital credentials. These may include licenses, permits, attestations, and certificates: secured, tamper-proof, and instantly verifiable.
It is part of the EU’s broader push for a trusted, interoperable digital infrastructure where identity, compliance, and business transactions move seamlessly across Member States.
How 4Sure brings the European Business Wallet to life
Our 4Sure European Business Wallet delivers all core EBW capabilities and more:
- Secure storage of verifiable business credentials such as company licenses, ISO attestations, permits, or ESG compliance proofs, using the latest eIDAS-compliant technologies.
- Cross-border interoperability through full support for European digital identity and wallet standards (eIDAS 2.0, OpenID Federation, DIIP, and EBSI profiles).
- Real-time credential verification via our Trust Registry and audit-proof infrastructure.
- Seamless integration with government and private sector services, allowing businesses to automate compliance checks and participate in digital-first processes.
- Custom branding and multi-role support, suitable for large enterprises, SMEs, trade associations, and public bodies managing credentials on behalf of members.
For more insights on the benefits of digital credentials, read our full post on Business benefits of eIDAS solutions.
More than a Wallet: it’s a gateway to EU-Wide Digital Trust
The 4Sure European Business Wallet is not a standalone app. It is part of a broader digital trust ecosystem that includes:
- Federated Trust Registries: Know exactly who issued a credential, under what policy, and whether they are authorised to do so.
- Compliance and audit tooling: Make verifiability auditable, without compromising data minimisation or privacy.
- Hosted or self-deployed options: Run the wallet infrastructure under your control, or rely on 4Sure as your managed provider.
Why it matters now
As the European Commission sets the stage for a fully digital, interoperable single market, businesses need to prepare for a future where credentials replace paper, and trust is digital, standardised, and immediate.
The 4Sure European Business Wallet is your path to be ready, whether you’re a regulatory authority, (semi-)public organization, large enterprise, MSP, or SME.
