Wallets for people
and organisations
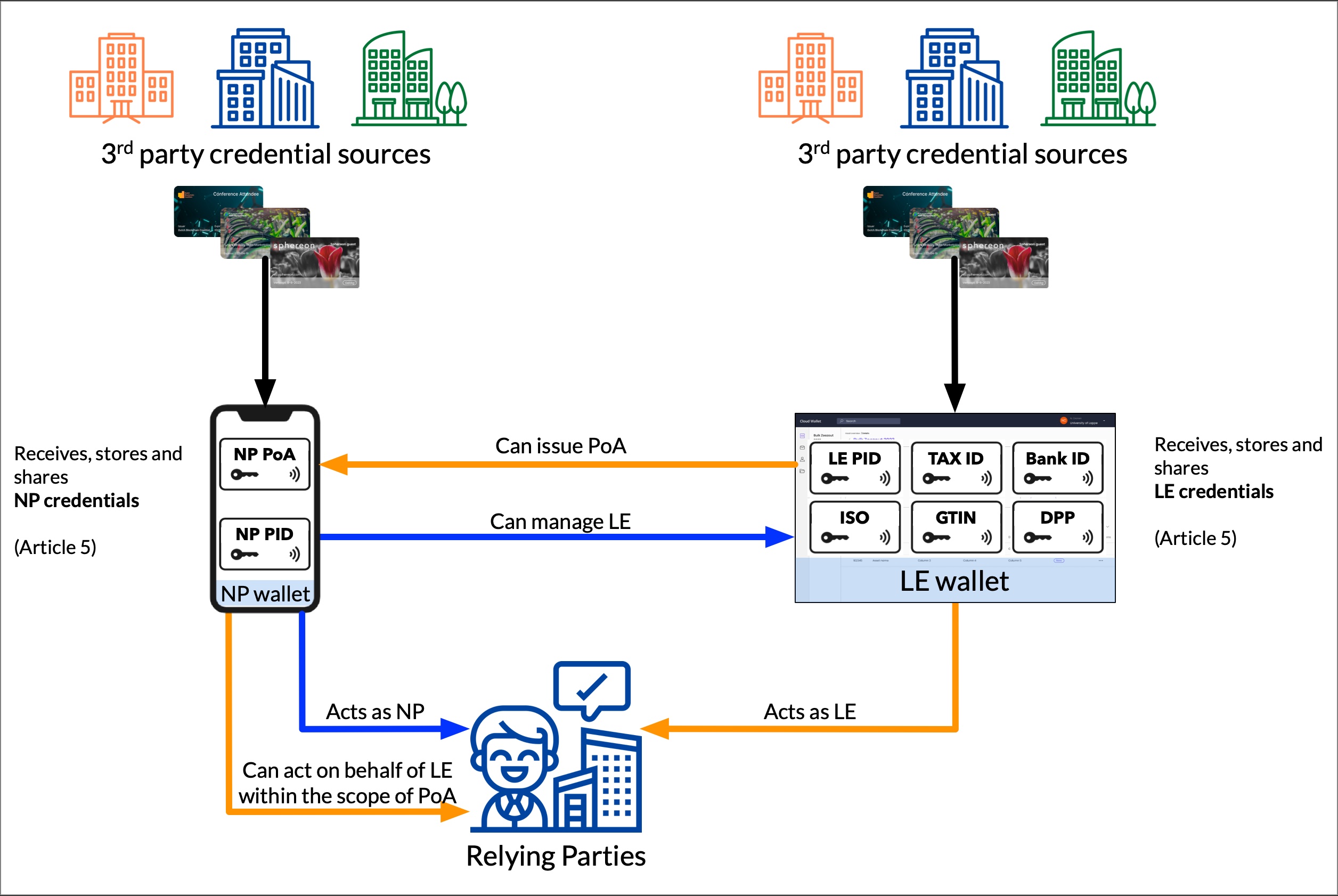
The overview here offers a view of a digital identity system that’s designed to streamline the verification and management of credentials for both natural persons (NPs) and legal entities (LEs). It is crafted in line with Article 5 of the new eIDAS 2 regulation.
- 3rd Party Credential Sources: There are multiple credential sources, some credentials are meant for and issued to natural persons (left) and others for legal entities (right).
- NP Agent & Wallet: Receives, stores, manages, and shares credentials related to natural persons.
- LE Agent & Wallet: Functions similarly but for legal entities, storing, managing, receiving, and sharing credentials but pertinent to businesses or organisations. These may include legal entity identifiers, tax IDs, bank IDs, and other certifications such as ISO standards and product identifiers like GTIN.
- Power of Authority: A business or organisation may use their Legal Entity Wallet to issue Power of Athority (PoA) credentials for specific transactions to specific Natural Persons, like officers, employees, or external representatives.
- Relying Parties: These are the individuals or entities that have a legitimate need for these credentials, possibly to verify the identity or receive certain data of natural persons and legal entities.
- Acting as NP: A Natural Person can obviously act for themselves.
- A NP acting on behalf of a LE: But a Natural Person can also perform actions on behalf of legal entities but only within the scope of the PoA.
- A NP managing a LE: A Natural Person can manage one or more LE Wallets. The natural person must provide credentials that prove for which actions they are authorized by the business or organisation.
- Acting as LE: Based on Article 5 of the eIDAS 2.0 regulation (below), there is legal requirement for legal entities to control their own data and to be able to perform transactions as a legal entity.
Article 5a of the eIDAS 2.0 regulation
This article outlines the framework for European Digital Identity Wallets (EUDI Wallets), and is directly relevant to organizations in several ways:
- Provision for Legal Entities: While the regulation ensures that all natural persons have access to secure and seamless cross-border digital services, it also specifically includes legal entities, which means that organizations and companies are also entitled to utilize these wallets for their transactions and digital interactions.
- Control Over Data: For organizations, having full control over their data is crucial. This can include control over corporate data shared during transactions, intellectual property, or sensitive business information. EUDI Wallets must be designed to not only give users but also legal entities this level of control.
- Operational Efficiency: By providing a common framework for secure requests, storage, and sharing of identification data and electronic attestations, organizations can streamline their processes. This is particularly significant for businesses that operate across EU borders and need to interact with various public and private services in other member states.
- Cross-Border Business Operations: The EUDI Wallets must support cross-border operations, enabling organizations to authenticate identity and attributes seamlessly across the EU. This is crucial for companies that have a multinational presence or those looking to expand into different EU markets.
- Secure Authentication of Entities: Organizations will be able to securely authenticate the identity of other entities — or people claiming to act on behalf of those entities — which is crucial for B2B transactions, partnerships, and supply chain management.
- Integration with Existing Systems: The regulation allows Member States to provide additional functionalities, including interoperability with existing national electronic identification means, which enables organizations to integrate the EUDI Wallet into their existing digital infrastructure.
- Voluntary Adoption: The use of the EUDI Wallet is voluntary, which gives organizations the discretion to choose the best tools for their specific needs without being mandated to adopt a particular vendor or wallet.
- Security and Privacy: The regulation’s emphasis on high assurance levels and strict data protection measures aligns with organizational needs to safeguard sensitive business information.
To summarize, Article 5a of the eIDAS 2.0 regulation lays the groundwork for a digital identity infrastructure that legal entities, such as organizations, can use to enhance their digital autonomy, streamline operations, and bolster security in their digital interactions across the European Union.